A minimal checklist for hardening (securely configuring) and optimization of a WordPress…
Software Security Introduction
Software security is critical to keeping information secure and achieving the desired level of cybersecurity, and this can only be accomplished by implementing the appropriate security and specialized practices at all stages of the software development life cycle (SDLC). We are surrounded by interconnected computers (including embedded systems) that run software that can be exploited for unintentional or malicious use, causing serious damage to society or business. Network security is ineffective at reducing the risk of these threats, and software security practices should be implemented throughout all phases of the software life cycle (from software requirements analysis to software qualification testing). This article provides an overview of the practices that should be followed at all stages of the software life cycle.
Keywords: Software Security, Static Analysis, Dynamic Analysis, Binary Analysis, Secure Requirements, Software Vulnerabilities, Software Defects, Software Life Cycle, Application Software.
Introduction
A Computer is a functional unit that can perform significant computations, such as numerous arithmetic and logic operations, without the need for human intervention [1]. A computer is made up of hardware and software.
Hardware refers to the physical components that can be seen and touched (e.g., hard drive, mouse, keyboard, etc.).
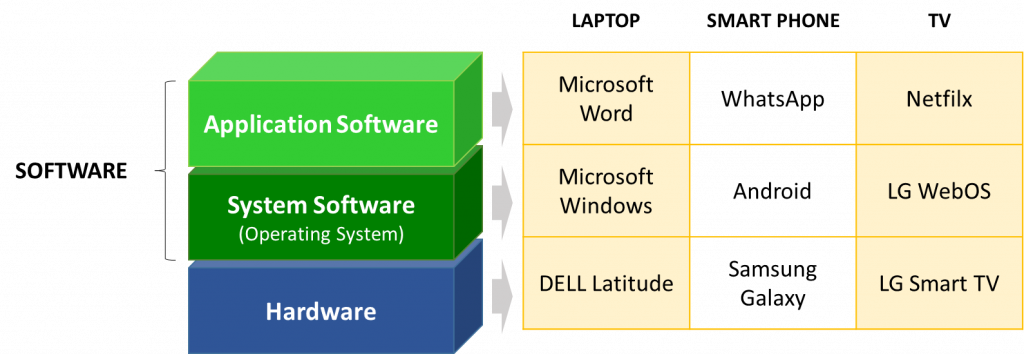
Software (also known as a computer program) is a set of instructions and data definitions that allows a computer to perform computational or control functions (i.e., arithmetic operations and logic operations without human intervention). The software may contain procedures, as well as associated documentation and data, pertaining to the operation of a computer system [1]. The software can be classified according to its intended use. System Software and Application Software are the two main types of software. System Software, such as the operating system, is software designed to manage the computer itself. Application Software, as opposed to system software, is software designed to assist users in performing specific tasks or dealing with specific types of problems [1]. Figure 1 depicts three examples of common computers and software. More examples of computers (i.e., embedded systems) in our daily lives can be found in my article Embedded Systems Security [9].
Software Security and Vulnerabilities
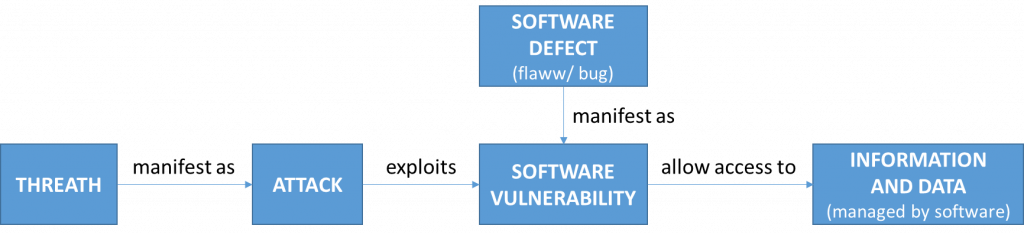
Software must be secure, which means it must be capable of protecting information and data in such a way that unauthorized people or systems cannot read or modify it, and authorized people or systems are not denied access to it [2]. The collection of all activities to be performed on the software to make it secure, in other words, providing the software with the ability to protect the information and data it manages from accidental or malicious access, use, modification, destruction, or disclosure [1], can then be defined as Software Security. A threat is any circumstance or event that has the potential to negatively impact the information managed by the software through unauthorized access, destruction, disclosure, data modification, and/or denial of service. The software may have weaknesses (i.e., Software Vulnerabilities) depending on how it is designed and implemented, and threats may exploit these weaknesses by using, modifying, destroying, or disclosing the information that the software manages [3]. To prevent their exploitation, software vulnerabilities should be detected, identified, evaluated, and properly treated, with appropriate and timely action taken to address the security risks described above [4]. We are surrounded by computers (including embedded systems [9]), and as a result, software vulnerabilities can be exploited for unintentional or malicious use, modification, destruction, or disclosure of sensitive (e.g., employee records, facility plans, intellectual property, financial data, etc.) and protected (e.g., medical records, bank statements, credit reports, genetic data, etc.) data. This is the primary reason why we must ensure that the software, as defined above, is secure.Security Throughout the Software Life Cycle
Figure 2 depicts the software life cycle, which consists of four major processes: software implementation, software operation, software maintenance, and software disposal. In each of these processes, software security must be ensured through the use of specific professionals, methodologies, and technologies.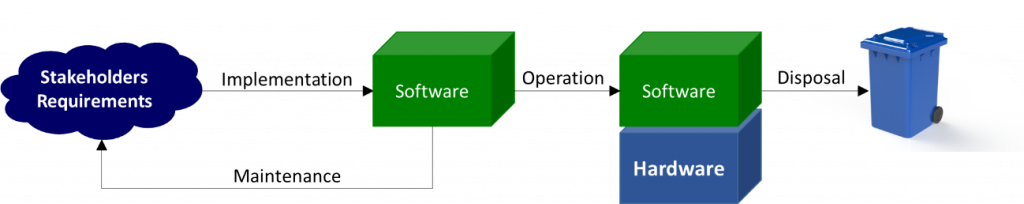
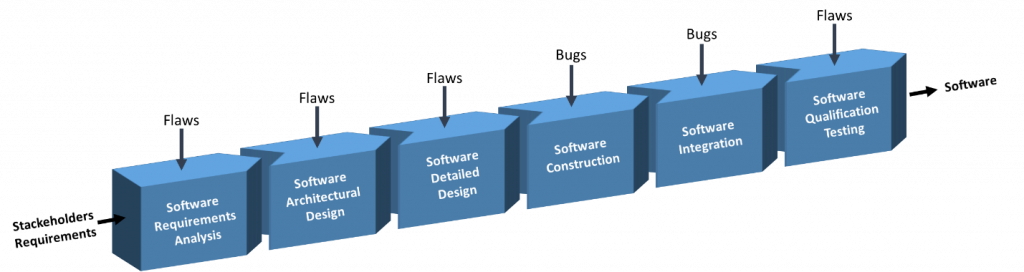
Software is created through a process known as Software Implementation (also known as the Software Development Life Cycle ( SDLC)) that transforms the requirements and constraints of specific stakeholders (e.g., users, owners, operators) into intermediate elements via coordinated activities. The software that meets the initial requirements and constraints through verification and validation is the end result of the software implementation process. The primary activities of the software implementation process (Figure 3) are Software Requirements Analysis, Software Architectural Design, Software Detailed Design, Software Construction, Software Integration, and Software Qualification Testing, with the following goals in mind [5]:
- Software Requirements Analysis, to establish the requirements of the software.
- Software Architectural Design, to provide a software design that implements and can be verified against the requirements.
- Software Detailed Design, to provide a software design that implements and can be verified against the requirements and architecture of the software and is sufficiently detailed to allow for coding and testing.
- Software Construction, to produce executable software units that accurately reflect the design of the software.
- Software Integration, to combine software units and software components, to produce integrated software elements that are consistent with the software design, to demonstrate that the functional and non-functional requirements of the software are met on an equivalent or complete operating platform.
- Software Qualification Testing, to confirm that the integrated software product satisfies its defined requirements.
There are additional support processes that we are not listing here for the sake of brevity.
Software vulnerabilities are caused by software flaws introduced during the software implementation process (Figure 3). Bugs are software defects introduced during the Software Construction and Software Integration phases, whereas flaws are software defects introduced during the Software Requirements Analysis, Software Architectural Design, and Software Detailed Design phases [7]
As shown in Figure 4, it is useful at this point to summarize the main elements introduced thus far, as well as their relationships.
Software defects (i.e., vulnerabilities) should be detected, identified, evaluated, and removed concurrently with each activity of the software implementation process, and in any case before the end of the activity and the start of the next activity.
The Financial Advantages of Securing Software
In Jerry Maguire ‘s movie, Rod Tidwell asked, “Show me the money!” We ‘re right here. A software defect, other than potentially result as software vulnerability, is a waste in software product implementation because it adds no value to the software product in the eyes of the customer and only adds cost and time” (Womack and Jones, 1996). For these reasons, early detection and correction of software defects along with software implementation, it is essential to increase the overall level of software security and minimize the cost of software production. A defect (i.e., vulnerability) introduced during the implementation process of the software may exponentially generate other vulnerabilities, either directly or indirectly, in subsequent activities, and, in the event that it is found at a later stage, the software may require redesign and reconstruction. This iterative cycle is costly in terms of time and resources. In order to truly understand security threats to software, security needs to be addressed in the earliest stages of the software implementation process. A study conducted by the IBM System Science Institute [6] showed that fixing a defect introduced during the initial stages of software implementation would cost 6 times more if detected during software construction/integration, would cost 15 times more if detected during software testing, and would cost 100 times more if detected during software maintenance (Figure 5).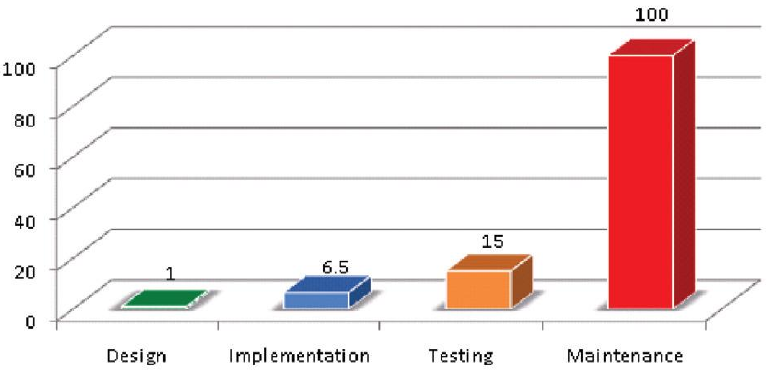
Conclusions
We are surrounded by interconnected computers (including embedded systems) that run software that can be exploited for unintentional or malicious use, causing serious damage to society or business. Network security is ineffective at reducing the risk of these threats, and software security practices should be implemented throughout all phases of the software life cycle (from software requirements analysis till the software qualification testing).
Early detection and correction of software defects, as well as software implementation, are critical for increasing overall software security and lowering software production costs. According to studies, fixing a defect (or vulnerability) introduced during the early stages of software implementation would cost 6 times more if discovered during software construction/integration, 15 times more if discovered during software testing, and 100 times more if discovered during software maintenance.
References
[1] ISO/IEC/IEEE 24765 Systems and software engineering — Vocabulary.
[2] ISO/IEC 9126 Software engineering — Product quality.
[3] National Information Assurance (IA) Glossary, Committee on National Security Systems (CNSS), 2015.
[4] ISO/IEC 27002 Information technology — Security techniques — Code of practice for information security controls.
[5] ISO/IEC 12207 Systems and software engineering — Software life cycle processes.
[6] Integrating Software Assurance into the Software Development Life Cycle (SDLC) – Maurice Dawson, Darrell Norman Burrell, Emad Rahim, Stephen Brewster, 2010.
[7] Secure Software Engineering: Learning from the Past to Address Future Challenges – Daniel Hein, Hossein Saiedian, 2009.
[8] ISO/IEC/IEEE 90003 Software engineering — Guidelines for the application of ISO 9001 to computer software.
[9] Embedded Systems Security – Andrea Desantis, 2020





This Post Has 0 Comments