A minimal checklist for hardening (securely configuring) and optimization of a WordPress…
Identification Of Software Security Vulnerabilities
The identification of software security vulnerabilities is not often easy and to facilitate it here I present a reference model, databases, metrics, and relationship between CVE, CVSS, CWE, CWSS, OWASP, and SANS standards. Many organizations and communities create and maintain a wide range of standards, databases, metrics, and classifications in order to identify, describe, publicize, and assess the severity of software vulnerabilities. Because of this plethora of entities and information, it is frequently difficult to understand the distinctions and relationships between them. The purpose of this article is to clarify these.
Software Security Vulnerabilities Reference Model
Software security vulnerabilities are identified, classified and their severity measured, based on international databases, standards, and methodologies as depicted in Figure 1, in a simplified but useful way.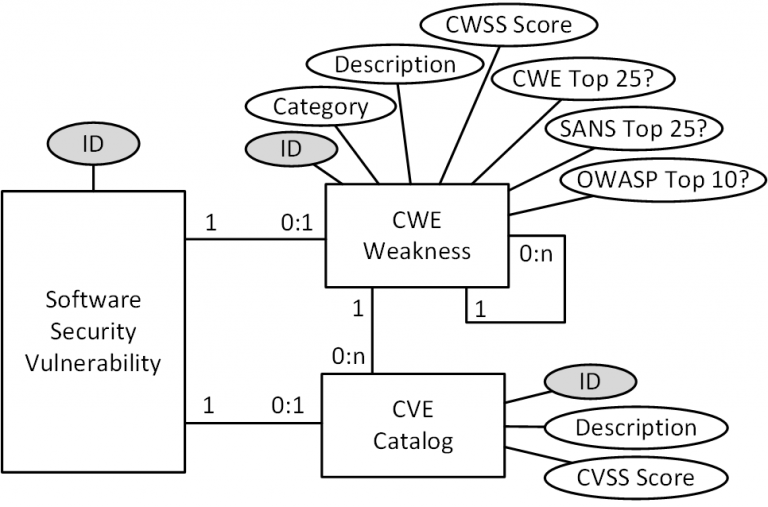
Common Weakness Enumeration (CWE) [1] – This is a list of types of vulnerabilities and defects in software and hardware, developed and maintained by the international community that serves as a common language, a yardstick for security tools, and as a basis for identifying vulnerabilities and defects and their prevention and mitigation. Each type of vulnerability in this list has a unique identifier, belongs to a category, has a description, and has a numerical severity calculated through a specific metric (CWSS – Common Weakness Scoring System) [2] based on three sub-metrics: Base Finding, Attack Surface and Environmental. The twenty-five vulnerability types with the highest CWSS severity are included in a list called CWE Top 25 [3].
Common Vulnerability Scoring System (CVSS) [5] – It is a free and open industry standard for assessing the severity of security vulnerabilities in information systems. The CVSS provides a metric and quantitative measure of the severity of a specific vulnerability with values between 0 and 10 and is considered the current standard for measuring and modeling risk related to application vulnerabilities. The severity measure is composed of a base score (CVSS Base Score [6]) and other (optional) temporal and environmental scores that allow taking into account respectively the availability of mitigations and the prevalence of vulnerable systems within an organization.
Open Web Application Security Project (OWASP) [7] – Is an online community that produces freely available articles, methodologies, documentation, tools, and technologies in the field of web application security including OWASP Top 10 and OWASP Mobile Top 10.
OWASP Top 10 [8] is a list of the ten web application vulnerability classes (not all software applications) that expose you to the greatest security risks where risk is calculated based on a combination of vulnerability frequency, vulnerability severity, and potential impacts. The vulnerability list is created, reviewed, and approved by an international community of security experts.
OWASP Mobile Top 10 [9] is a list of the ten mobile application vulnerability classes (not all software applications) that expose you to the greatest security risks where risk is calculated based on a combination of vulnerability frequency, vulnerability severity, and potential impacts. The vulnerability list is created, reviewed, and approved by an international community of security experts.
SANS [10] – A privately owned company specializing in cybersecurity training periodically produces the SANS Top 25 report [11] which is, based on their analysis and evidence, a list of the twenty-five vulnerability classes of software applications in general that expose you to the greatest security risks where the risk is calculated based on a combination of the frequency of vulnerability occurrence, the severity of the vulnerability, and potential impacts. The vulnerability list is created, reviewed, and approved by an international community of security experts. The list of vulnerabilities in the SANS Top 25 [3] report is almost identical to the list of vulnerabilities in the CWE Top 25 report [3].
Identification and Analysis of Software Vulnerabilities
Software security vulnerabilities identification and analysis can be carried out either statically or dynamically. In the first case, the software is examined without executing the program while in the second case it is examined by executing the program. For our purpose, we will focus only on the static mode and in particular on the Static Analysis and the Analysis of Software Composition.
Static Analysis (SAST)
Static analysis of source code, also known as static analysis or SAST, is a method for identifying and analyzing security vulnerabilities in software that is done by examining the code but without running the program. Typically, this activity is performed with the help of automated tools (SAST tools) that, in addition to providing an understanding of the code structure, help identify security vulnerabilities and non-conformities present in the software and ensure that the software adheres to international security standards.
Software Composition Analysis (SCA)
Software composition analysis, also referred to as software dependency analysis or SCA for short, is a method for identifying and analyzing the security of software components (for the purpose of this guideline OSS frameworks and libraries) that is performed by examining the code but without running the program. Typically this activity is performed with the help of automated tools (SCA tools) that identify and analyze open-source frameworks and libraries that are contained in and used by the software, including related artifacts such as containers and registries. In addition to identifying the security vulnerabilities of these components, non-compliance in terms of licensing and applicability within the organization is also identified. The SCA tool generates an inventory report of all open-source components present in the scanned software, including all direct and transitive dependencies. Once all open-source components have been identified, the tool provides information about each component including license details, attribution requirements, and whether that license is compatible with the organization’s policies. One of the key functions of the SCA tool, moreover, is to identify open-source components with known vulnerabilities, which allows you to assess and plan for a possible upgrade or replacement of those components.
References
[1] Common Weakness Enumeration (CWE)
[2] Common Weakness Scoring System (CWSS)
[3] CWE Top 25
[4] Common Vulnerabilities and Exposures (CVE)
[5] Common Vulnerability Scoring System (CVSS)
[6] CVSS Base Score
[7] Open Web Application Security Project (OWASP)
[8] OWASP Top 10
[9] OWASP Mobile Top 10
[10] SANS
[11] SANS Top 25
[12] Software Security, Andrea Desantis, 2020





This Post Has 0 Comments